| s |
| Home |
| Unix |
| Security |
| Publications |
| Links |
| About Site |
TCP/IP Ports
What are they? Why are they important to me?
Version .1
We (IT folk) install applications on our machines regularly, yet many still donít fully understand what is really happening to make the communications between a client and a server work. I hope to illustrate in words and pictures the communications process of some Internet applications. I will try to make this explanation as simple as possible so that even non-IT folk may understand. I will be using a few examples; HTTP, FTP, and an Telnet Client session to a Telnet Server.
First lets begin with a brief introduction to TCP/IP. TCP/IP is not a single protocol but actually a suite of protocols. What this means is that TCP/IP is a collection of protocols. To think of TCP/IP in a graphical sense can be helpful, TCP/IP can be pictured as a stack of blocks on top of each other.
 |
OSI Reference Model
|
Each Layer can only communicate to the layers directly in contact with it. Layer 1 cannot communicate with layer 3 without passing the contents to layer 2. This ingenious architecture allows for specialization amongst the layers. This design also allows for the introduction of other intermediate layers. You may already be using an application that inserts itself into your TCP/IP stack. Maybe you are using ZoneAlarm or Intel NetStructure VPNor something like it. These applications place themselves in the TCP/IP stack and intercept your packets and interpret whether it is destined for the Public Internet or to a Private Network using a VPN connection.
So what does this all mean to you? Well it means that the TCP/IP Suite is important and if you really want to harness the power of TCP/IP you must understand it further.
 |
This is a representation of where the
protocols reside in the protocol stack.
Notice on the left where the protocols we are so familiar with reside. FTP and HTTP reside in the Application layer.
|
Introduction to commonly known ports
Before we jump in. What is a port? A port can be thought of as a doorway into a computer. Network Applications that use the TCP/IP suite utilize sockets to communicate with one another. A socket is the combination of an IP address and a port.
You can envision a socket like the following illustration:
So, on the one hand you have an IP address, say 10.1.1.1 and a service port like 25 for SMTP. When a client connects to 10.1.1.1 on port 25 a "Socket" is created. This socket is an agreed upon pathway for communications made up of an IP address and a port number. In this case 10.1.1.1:25
If you have worked in IT for any amount of time you will be familiar with all if not most of the following ports. If you are not familiar with these ports, make your self comfortable with them now. If you can memorize any number of ports these are the key ones to remember.
Some of the more common port numbers are 21, 25, 53, 80 110, 443
21 = FTP: File Transfer Protocol
23 = Telnet: Telnet
25 = SMTP: Simple Mail Transfer Protocol
53 = DNS: Domain Name System
80 = HTTP: Hyper Text Transfer Protocol
110 = POP3: Post Office Protocol version 3
119 = NNTP: Net News Transport Protocol
443 = SSL: Secure Sockets Layer
Sometimes protocols are merged into an existing application. For example the Web Brower. The web browser sometimes acts as an ftp client. Whenever a web browser acts as an ftp client the URL typically looks something like ftp://ftp.ortizonline.com. Notice how its not http?
Whenever we send email using outlook express or some other email client, SMTP is almost definitely your tranfer protocol. There are exceptions like old MS-Mail clients and Old Lotus systems. Some companies use Outlook with only the Exchange service installed and this makes it unnecessary for the clients to communicate via SMTP. Although any server that wishes to be able to send email to ANYONE will need to speak SMTP.
Lets go on to analyze a sample Web Browsing Session.
1. User Launches her web browser and types in http://www.ortizonline.com
2. The Web Browser requests that the name www.ortizonline.com be converted to an IP address. Iíll explain DNS if time permits.
3. Once the browser has the IP address it will then connect to the machine using that IP address. The browser itself normally does not show this IP address. The browser will continue to show us the name. IP is necessary because itís the only way that the Routers on the Internet would know how to relay the packet to other routers.
4. Web Servers by default use port 80, although web servers can be made to listen on different port numbers. Web Browsers were programmed with this knowledge, so when a user types in a web site the web browser automatically connects to www.ortizonline.com using port 80. Ever noticed that some web sites have a colon and number after the url such as http://www.someserver.com:8000 all this means is that when someone installed the web server they changed the default port from 80 to 8000. This is also a way to install multiple web servers on one physical machine. It is possible to install Apache on port 90, IIS on port 91 and iPlanet on port 92. Very useful if only one server is available.
5. Once a connection request is made of the server, the client assigns a communications port. This is very important to understand, just because the Server is listening on port 80 doesnít mean that it talks back to the browser on port 80. This would be a really bad thing, since if you had a web server installed on the machine that was making the request, the Web Server www.ortizonline.com would try talking back to port 80 and fail to communicate with the browser. This is why the Web Server picks a random port number to talk back to the web browser.
6. Type netstat at a command line right after surfing to www.ortizonline.com. You should see something like;
TCP mirage:1372 vnt4.webhosting.com:80 ESTABLISHED
TCP mirage:1374 vnt4.webhosting.com:80 ESTABLISHED
a. The TCP above means its connecting using TCP.
b. Mirage is the name of my machine.
c. Port 1372 is a port assigned to the client side, this is the port that the server will send information to.
d. Vnt4.webhosting.com is the translated name for the server hosting www.ortizonline.com
e. Port 80 is the port number that the connection is using to communicate with the server.
f. ESTABLISHED means that the connection is still connected.
g. Port 1374 is there because I made 2 connections to www.ortizonline.com
7. If you click REFRESH on your web browser a few seconds later and run netstat again you will notice different client side port numbers. New Number will be assigned as you surf to different places and/or the same site.
8. That concludes our analysis of a user surfing to a site.
Similar to the previous example, FTP works in the same fashion. When a user
connects to an FTP server with an FTP client, the Client connects to port 21 and
another port is assigned to the client.
Why is this useful to know?
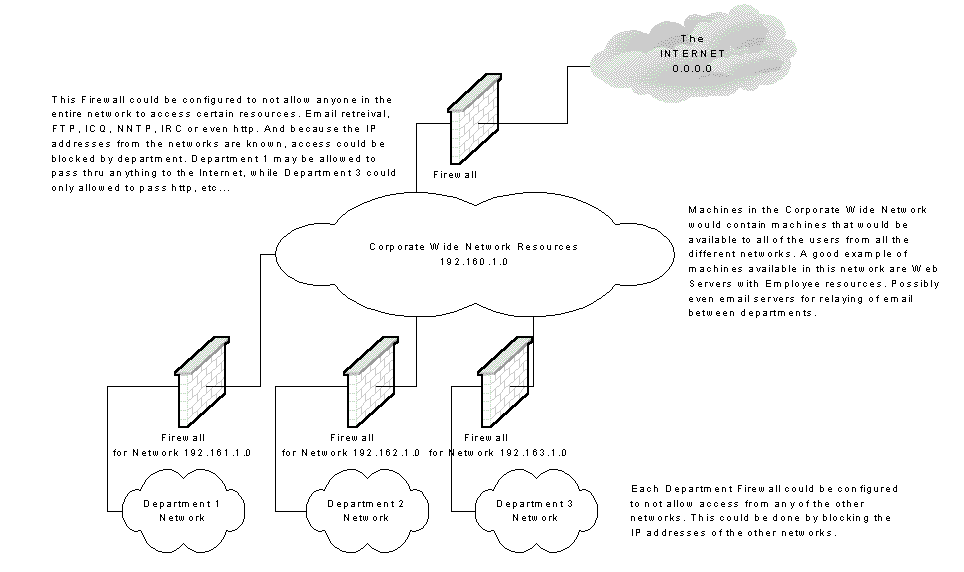
Firewall Reasons
One of the techniques commonly used with firewalls is the blocking of ports in order to conform to corporate security policies. For example, a company may block all connections to port 23 if telnet is not allowed to machines outside of the corporate network. Firewalls are a whole separate subject all together. I'll cover them in a future article. To learn more about firewalls check out Building Internet Firewalls by Brent Chapman ISBN 1565928717. Excellent book.
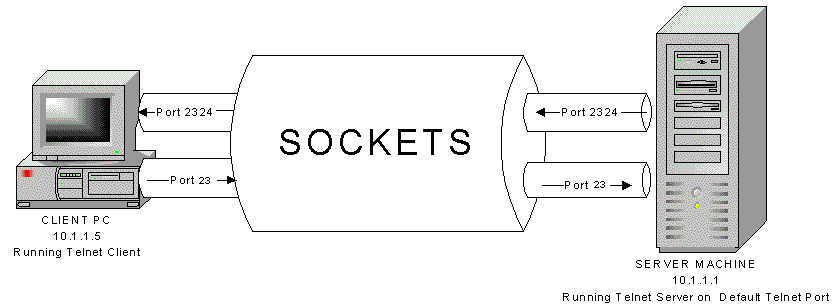
Lets use an example of a persistent client application such as telnet. telnet is a client application used to test that communications with a Telnet server is possible.
Assuming the Telnet server is installed to listen on its default port of 23(, we would do the following to connect with telnet.
1. Launch telnet and login to the system.
2. Run netstat to see what connection was made. You should see something like;
TCP mirage:1163 EMACHINE:23 ESTABLISHED
| TCP | mirage | 1163 | EMACHINE | 23 | ESTABLISHED |
| Protocol | Client Machine | Client TCP Port | Server Machine Name | Server TCP Port | Connection State |
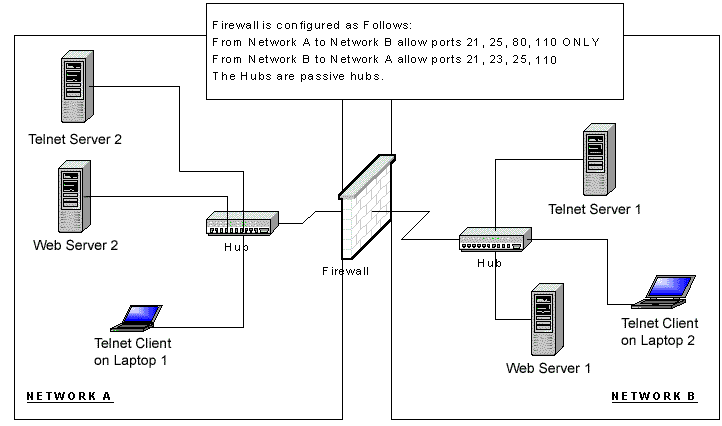
A. Will telnet on Laptop 1 be able to connect to Telnet Server 1 in this configuration?
B. Will telnet on Laptop 2 be able to connect to Telnet Server 2 in this configuration?
C. Will the Web Browser on Laptop 2 be able to look at web pages on Web Server 2 (assuming that Web Server 2 has been configured to use the default HTTP port)
D. Will the Web Browser on Laptop 1 be able to look at web pages on Web Server 1 (assuming that Web Server 1 has been configured to use the default HTTP port)
E. What needs to be configured on the firewall in order for telnet and Web Surfing to work in both directions?
Answers at the bottom of page.
Lets take a look at a simple telnet connection.

1. The telnet client connects to port 23 on the Telnet Server.
2. The port assigned for this connection is 2324. This means that when you type commands and send them to the Telnet Server any responses will be sent back to you via port 2324.
3. The connection from the Telnet Client would establish a socket connection which would be the Telnet Servers IP address and the port number (23). i.e 10.1.1.1:23
4. What would happen if the Telnet Server was reconfigured so that it listened on port 65? What would it look like?

5. The Telnet Client on the PC would have to be changed so that it created a "socket" using the IP address of the Telnet server and the new port number (65). i.e 10.1.1.1:65
How do hackers(crackers) leverage this knowledge of ports?
There are many port scanning tools, SuperScan is one of those such tools.
Here we have a screenshot of SuperScan
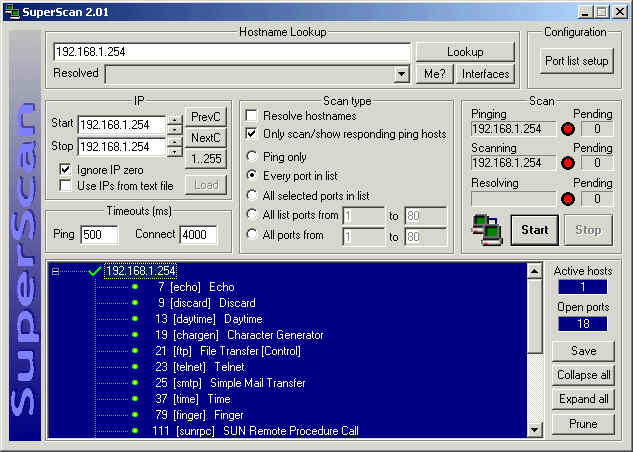
The machine scanned in this example is 192.168.1.254. By the results of the scan of 192.168.1.254 we can see that the ports available are:
192.168.1.254
___ 7 [echo] Echo
___ 9 [discard] Discard
___ 13 [daytime] Daytime
___ 19 [chargen] Character Generator
___ 21 [ftp] File Transfer [Control]
___ 23 [telnet] Telnet
___ 25 [smtp] Simple Mail Transfer
___ 37 [time] Time
___ 79 [finger] Finger
___ 111 [sunrpc] SUN Remote Procedure Call
___ 512 [exec] remote process execution;
___ 513 [login] remote login a la telnet;
___ 514 [shell] cmd
___ 515 [printer] spooler
___ 540 [uucp] uucpd
___ 6000 [x11] -6063 X Window System
___ 6112 [dtspcd] dtspcd
___ 7100 [font-service] X Font Service
By the number of ports on this machine, its possible to see this machine is running many, many services. By running SuperScan against 192.168.1.254, its clear to see exactly what services are servicing requests. So what information does this reveal? Lets try using telnet to telnet to port 23.

This telnet session reveals that the IP address 192.168.1.254 is a SUN 5.8 server.
The hacker(cracker) can then very easily go to http://www.cert.org/ and look up "SUN 5.8" or "uucpd" to see what vulnerabilities have already been discovered and reported. If the admin of 192.168.1.254 doesn't keep up with the patches, this machine will be fair game for the cracker.
So you see TCP/IP ports are an integral part of communications and security on the Internet.
Feel free to download a complete downloadable list of TCP/IP ports.
by DaKatana
Comments? Questions? Rants? Raves? Please send to the number6 at ortizonline dot com
A. No B. Yes C. No D. Yes E. Enable Ports 23 & 80 to both sides
|
|
|
|
|